I’ve been interested for a while in playing with ethernet switching on a hardware level, and decided to put together a platform to play with routing and switching hardware with a Raspberry Pi compute module, and an ‘off the shelf’ switching chip available commercially.
The switch chip I ended up choosing is the KSZ9477 from Microchip, with seven gigabit interfaces, including an SGMII interface for an SFP cage. While this device can’t hold a candle to the big-boy chips from Broadcom that a lot of the big network vendors use, I can’t source those, and the fundamentals should be reasonably accessible with the Microchip device.
The device is configured using Python scripts on the Pi talking SPI to the switch chip to configure ports, vlans, and read out things like the interface counters. The Pi can be configured with multiple VLAN interfaces to handle routing functions.
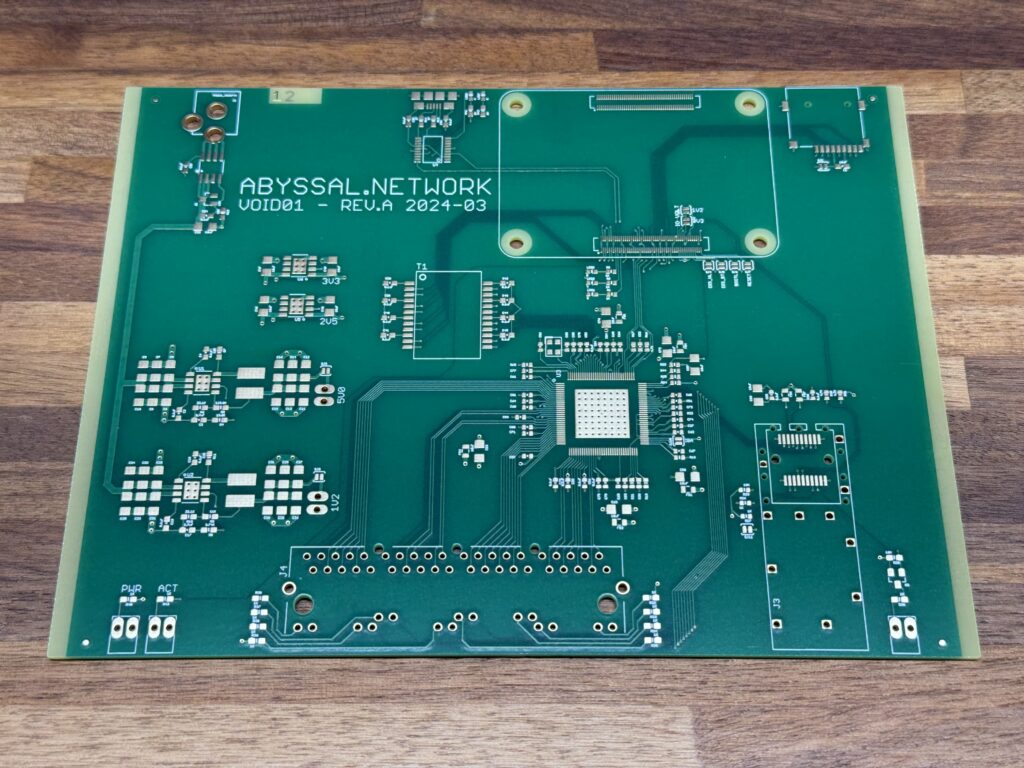
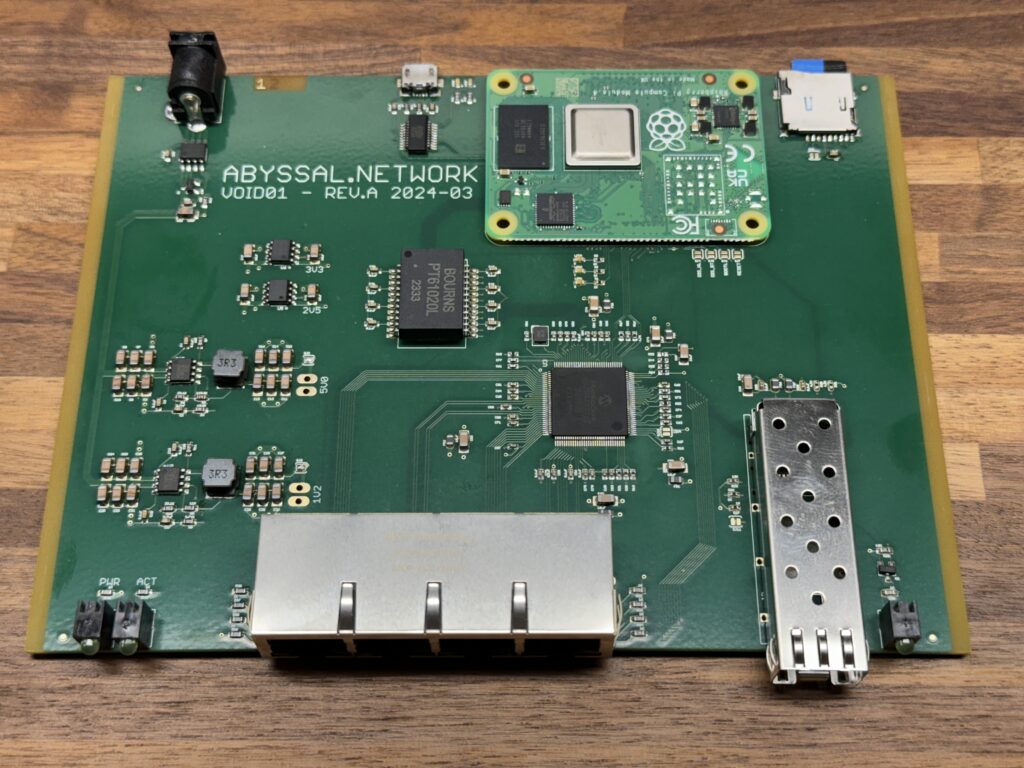

The hardware design files, and if I ever get around to it some of the software scripts, are available on GitHub.